
CONTENTS

Introduction to Integrity

Demystifying the Science

The Language of Data Forensics

How Does it Work?

Data Forensics & Certification

Lurking Test Security Threats

The Costs of Poor Security

What to do with Your Data Forensics Report

Talking to Your Organization about Data Forensics
Too many tabs open?
We’ve been there. Enter your email to get a permanent copy of this guide sent directly to your inbox.
Let's Talk About Integrity
So you’re curious about data forensics (DF)? Good. If you’re already thinking about the health of your assessment, especially when it comes to security, then you’re on the right track! Give yourself a pat on the back.
But what is data forensics? How does it work? What security threats and vulnerabilities actually apply to your assessment? Consider this your ultimate guide, which will walk you through the basics of statistical analyses and explore security vulnerabilities that may be hidden within your certification program. Keep reading to learn about the hidden costs of poor exam security, what you should do after you conduct data forensics, and (importantly) how to help your organization adopt this program-strengthening practice.
Here’s to integrity!
Demystifying the Science Behind Data Forensics
What are some classic psychometric statistics that data forensics experts use to pinpoint patterns and other clues in testing data?
1. Similarity
2. Answer Changes
3. Score Differences
4. Timing
5. Aberrance
6. Program-Specific Indicators

The Language of Data Forensics
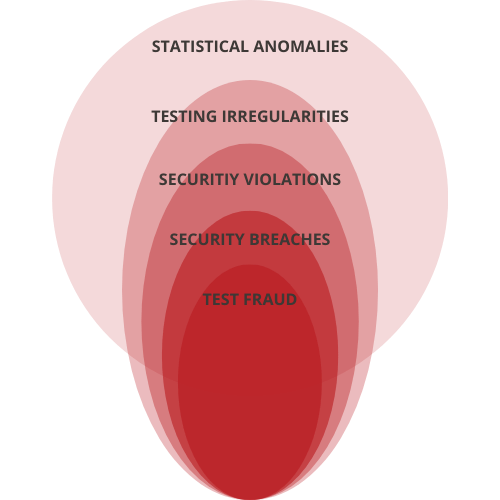
Statistical Anomalies
Example: Examinees demonstrating two different levels of proficiency
Testing Irregularities
Example: A fire alarm disrupts test takers during the testing window
Security Violations
Example: The seats in the testing room are too close together
Security Breaches
Example: Administrator accidentally discloses exam content to examinees
Test Fraud
Example: Administrator intentionally discloses answers to examinees
How Does Data Forensics Work?
The path to exam validity is different for every certification program, but there are several milestones every program meets on the journey to exam integrity.
1. Decide to Conduct Data Forensics
Whether you’ve experience a known incident, or you’ve decided to use data forensics for one of the reasons listed below, this is a critical first step.
2. Provide Data to Data Forensics Vendor
From basic response booklets to online answer-change and response-time data, your vendor will want whatever you can provide to strengthen the results.
3. Receive Results and, if Desired, Recommendations
You should work with your vendor ahead of time to decide what kind of results you want to receive and put together a general security plan for incident response.
4. Investigate Any Possible Security Threats
If your results show areas of potential vulnerability, work with your vendor to collect more evidence and investigate further.
5. Take Action, If Needed
If wrongdoing is uncovered by data forensics and proven in your investigation, then you should take the appropriate actions as outlined in your security plan.
Why Does a Certification Program Need Data Forensics?
Maintain the Value of Your Certification
Deter Test Fraud Before it Happens
Reveal Security Vulnerabilities
Highlight Instances of Test Fraud
Collaborate with Test Security Experts
Plan for the Future of Your Program
Security Threats Above and Below the Surface
Above the Surface
Examinee Collusion
Similarity statistics and source-copier statistics can sniff out examinees who peek at others’ exams or who share test content with other examinees.
Test Killers
Similarity statistics and flawed-key analyses detect the use of stolen exam content contained within “Test Killers,” distributed within small cheat rings and dispersed among test takers.
Administrator Collusion
Wrong-to-right answer-change and similarity analyses can help detect educators and exam administrators who commit test fraud.
Below the Surface
Large-Scale Collusion
Data forensics can detect large-scale examinee collusion and support disciplinary actions by testing programs against individuals in cases of test fraud.
Fraudulent Test Sites
Data forensics can detect test sites operated by pirates and fraudsters and can provide the necessary evidence for taking legal action.
Proxy Testers
Data forensics can uncover the illicit activity of proxy test-takers or professionals for hire, who take tests for others, and the candidates who employ them.

The Hidden Costs of Poor Exam Security
Want to take a copy of the guide to-go?
You don’t need a disposable lid, bag, or box. Just download here.
Check out Other Test Security Resources

Security Boot Camp Part 1: Preparedness

Security Boot Camp Part 2: Technology

Security Boot Camp Part 1: Preparedness

Security Boot Camp Part 2: Technology

Security Boot Camp Part 1: Preparedness

Security Boot Camp Part 2: Technology
Want to subscribe to our newsletter?